Apache has recently released an advisory regarding CVE-2023-50164, a critical vulnerability with a severity rating of 9.8 that affects Apache Struts 2. CVE-2023-50164 is intricately tied to an organization’s Apache Struts architecture and the way it uses its file upload feature, enabling unauthorized path traversal that could be abused to upload a malicious file and perform remote code execution (RCE). It should be noted that exploiting this vulnerability at scale becomes significantly challenging for attackers, as it lacks the same straightforward scanning and exploitation capabilities observed in CVE-2017-5638. Apache advises users to upgrade to Struts 2.5.33, 6.3.0.2, or higher.
Apache Struts is extensively integrated into various systems and has gained widespread attention via the infamous Equifax breach in 2017. The Equifax breach affected over 145 million people and led to the consumer credit reporting agency paying a US$700 million settlement. One significant aspect of the incident involved Equifax hackers stealing 200,000 credit card accounts in a single, sweeping attack.
What versions are affected?
This vulnerability impacts Struts versions ranging from 2.5.0 to 2.5.32 and 6.0.0 to 6.3.0:
- Struts 2.0.0 – Struts 2.3.37 (EOL)
- Struts 2.5.0 – Struts 2.5.32
- Struts 6.0.0 – Struts 6.3.0
Dissecting the vulnerability
The flaw permits an attacker to manipulate file upload parameters, opening the door to path traversal. This could potentially result in the uploading of a malicious file, enabling remote code execution. The vulnerable end-point is /upload.action as per the current scenario.
What’s occurring is a distinction in the treatment of parameters based on case sensitivity. For instance, the vulnerability views param1=”value1″ and Param1=”Value1″ as different due to the case-sensitive nature of HTTP parameters. Upon examining the recent commits from the Apache team, we found that they have changed the HTTP parameters to be case-insensitive (Figure 1).
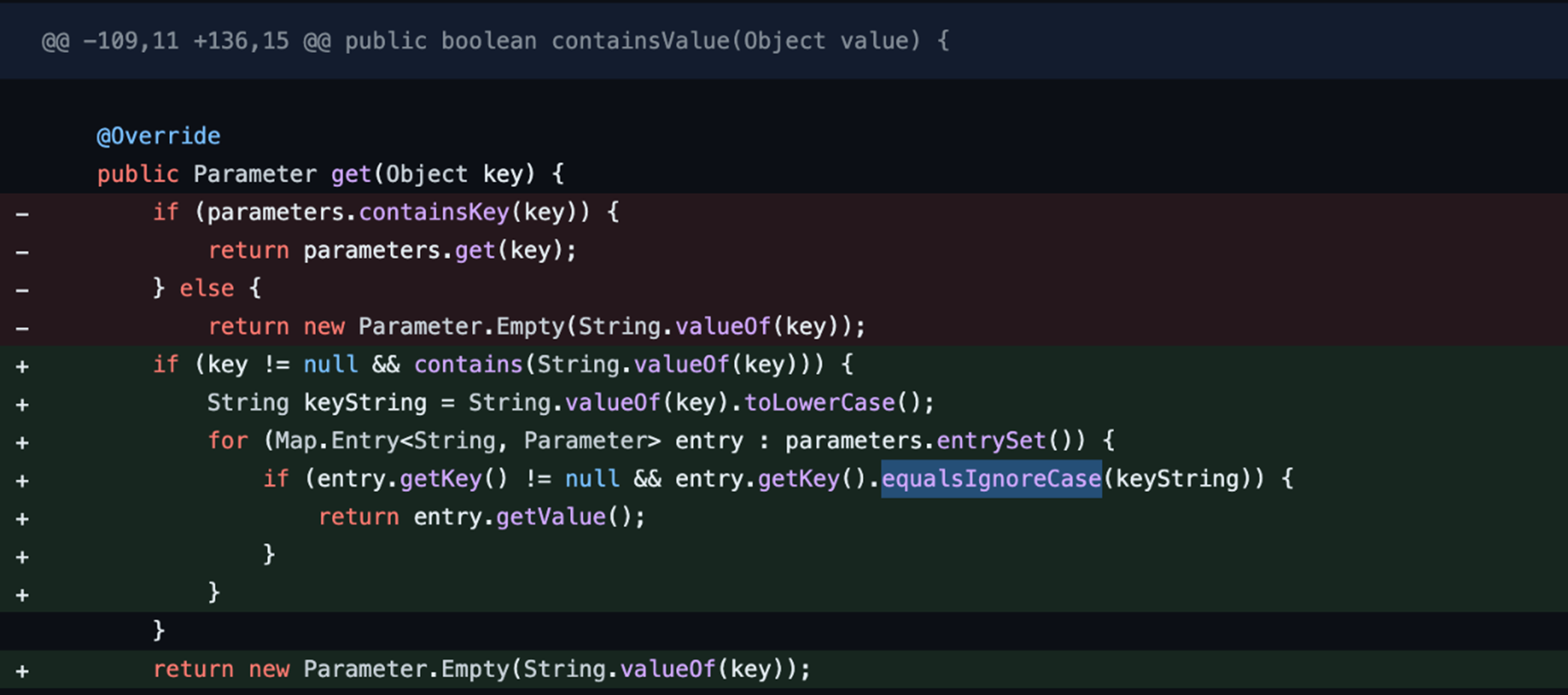
The vulnerability in Apache Struts arises from parameter pollution. In this scenario, an attacker can manipulate the request by modifying the initial parameter and subsequently introducing an additional parameter in lowercase. This lowercased parameter can then override an internal file name variable, leading to the exploitation of the system.
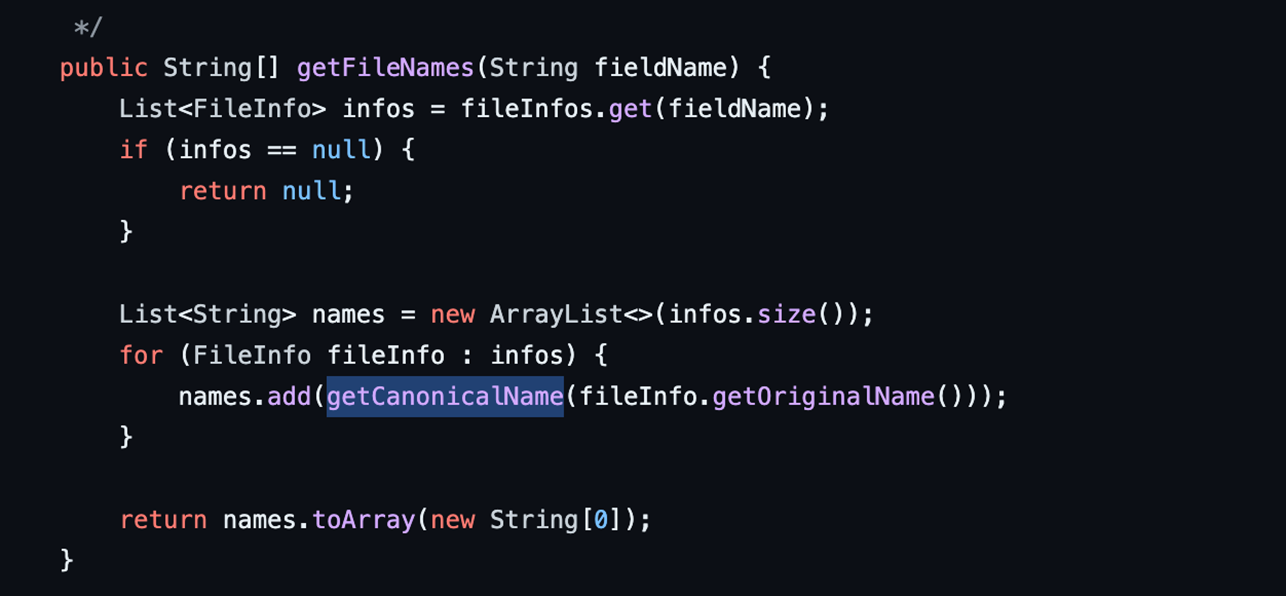
When the class ActionSupport processes arguments from the HTTP request, the manipulated filename value can have path traversal characters. The bug bypasses Apache Struts’s getCanonicalName function in AbstractMultiPartRequest.java, enabling the path traversal payload to persist in the final filename(getOriginalName()), as seen in Figure 2.
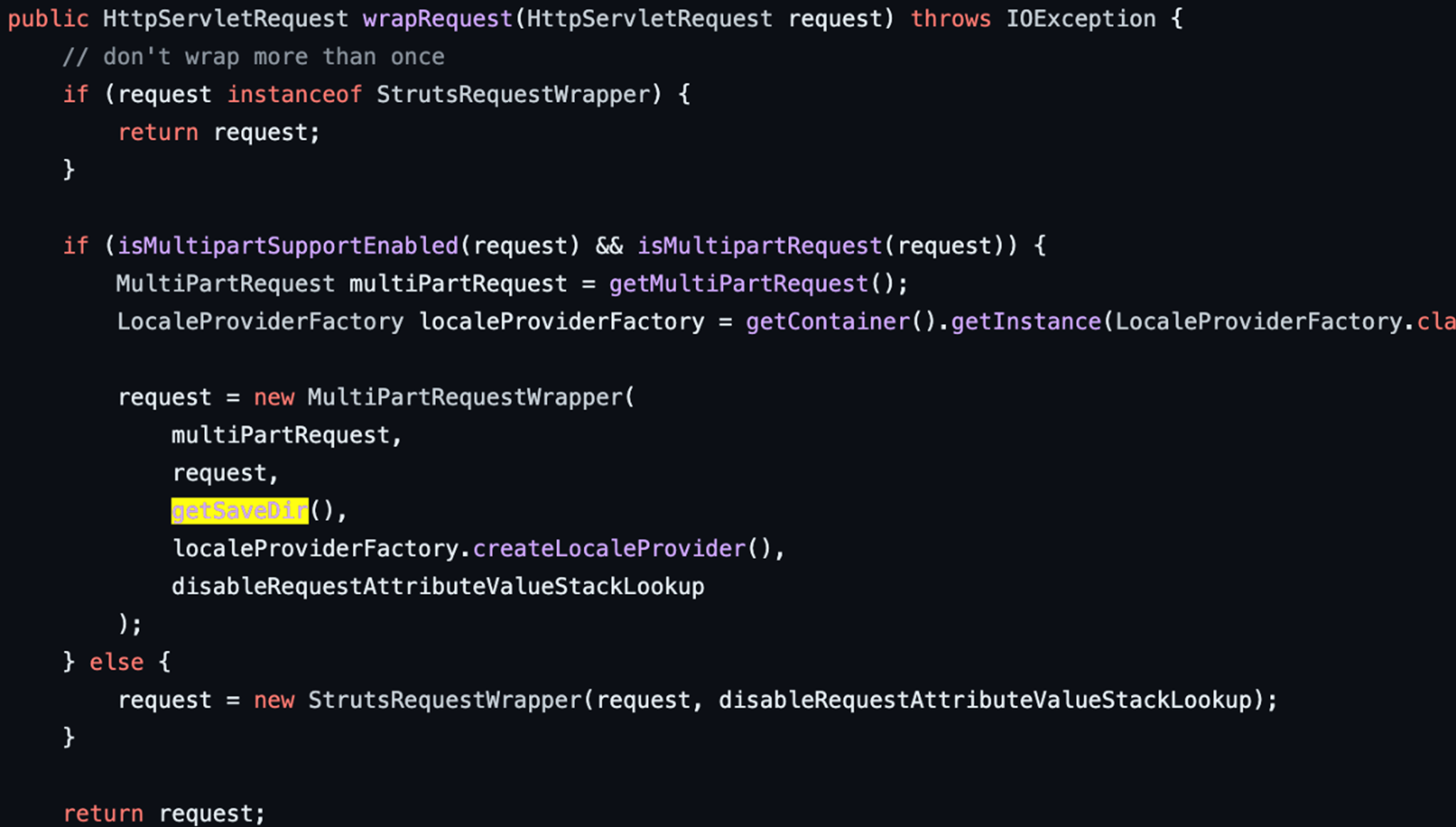
We have observed one more commit from the team about the deletion of the temporary files. Prior to this new commit, when files are uploaded, the getSaveDir function returns the specified path and generates a temporary file in temporary directory (Figure 3). However, these temporary files are sometimes not deleted if they exceed a certain file size, creating a potential security risk and allowing the threat actor to achieve persistence in the affected systems (Figure 4). This part could be used if we can control the file name of the temporary file.
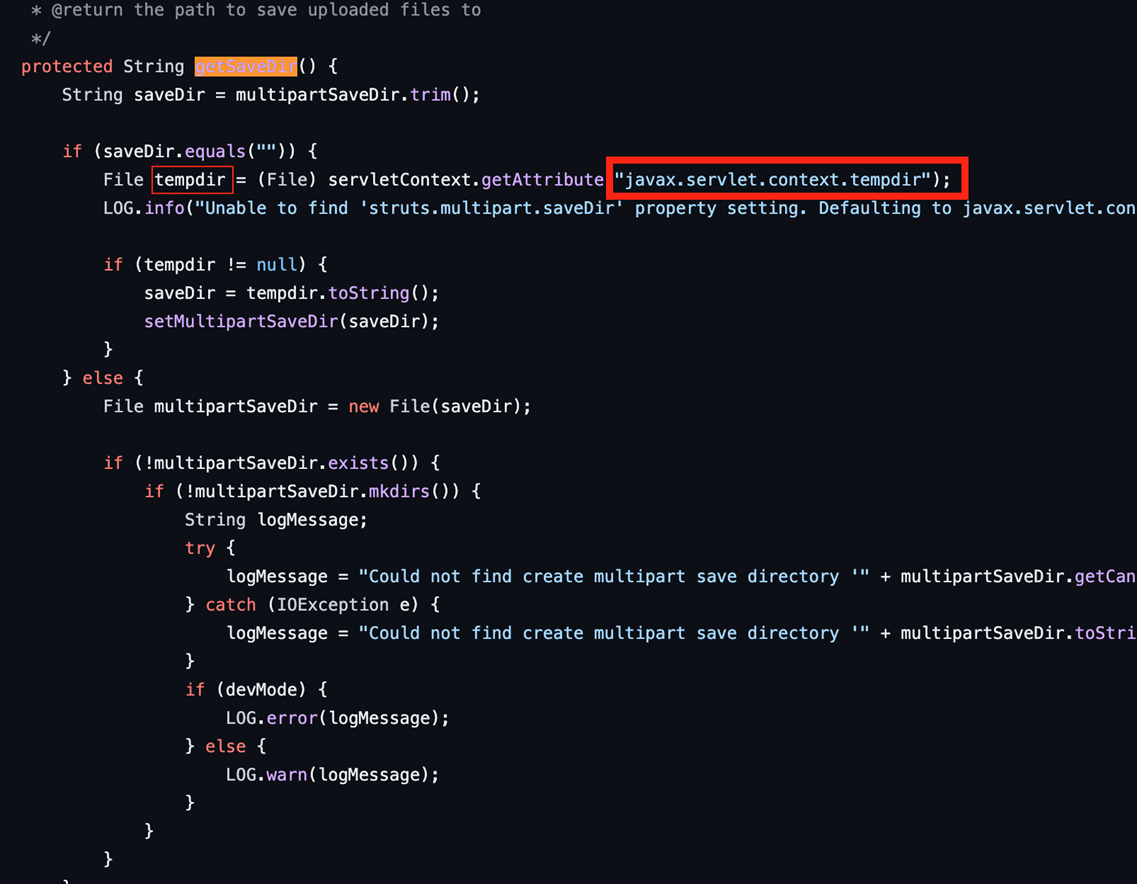
However, after the commit, we have determined that the commit was made to “Always delete uploaded file,” which would ensure that temporary files are correctly deleted after upload. According to another researcher’s detailed report, if the file size surpasses a certain limit, an error will be triggered with the message “struts.messages.upload.error.parameter.too.long.” Subsequently, the method prepare.cleanupWrappedRequest(request); will be executed. However, during the file generation process, the file is split into two when Item.add is applied. In the event of a file exceeding the size limit, exception handling will be initiated.
What the request looks like
With contributions from Brandon Evans
The request is shown below in Figure 5. Notably, the parameter is named “Upload”, mixed with uppercase and lowercase letters.
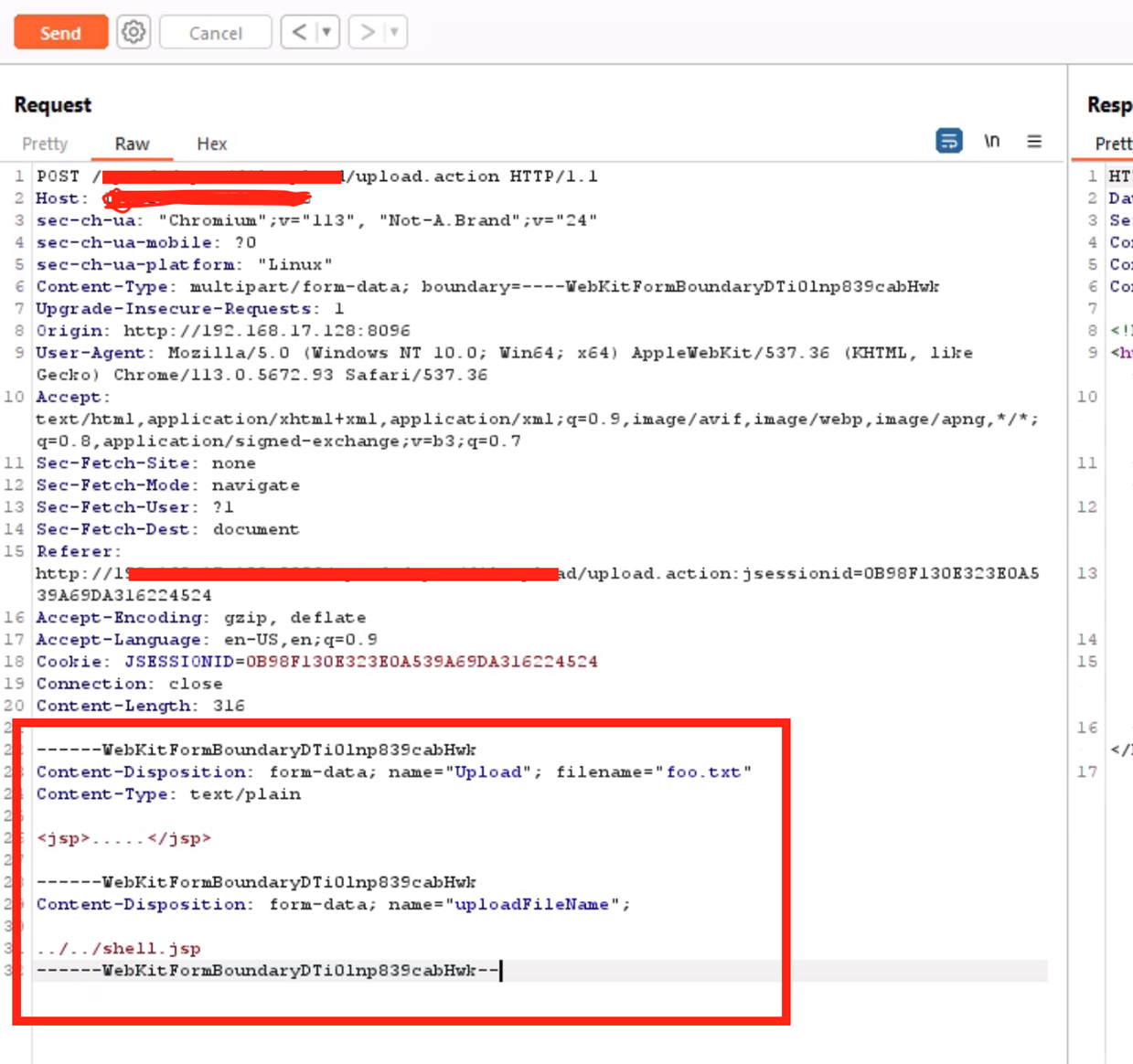
Conclusion
The CVE-2023-50164 vulnerability could be exploited by threat actors to perform malicious activities, representing a potential security risk for organizations. Leveraging security solutions such as Trend Vision One™️ can assist organizations in safeguarding their environment from threat actors and attacks like the one described in this entry.
Trend Vision One™ – Endpoint Security provides protection from any threats that may target this vulnerability via the following Deep Packet Inspection (DPI) rule:
- 1011933 – Apache Struts2 Remote Code Execution Vulnerability (CVE-2023-50164)
TippingPoint has posted a Customer Shield Writer (CSW) file for this vulnerability that is available for customers to download on TMC. The applicable rule is as follows:
- 43563: HTTP: Apache Struts 2 Code Execution Vulnerability
Tags

